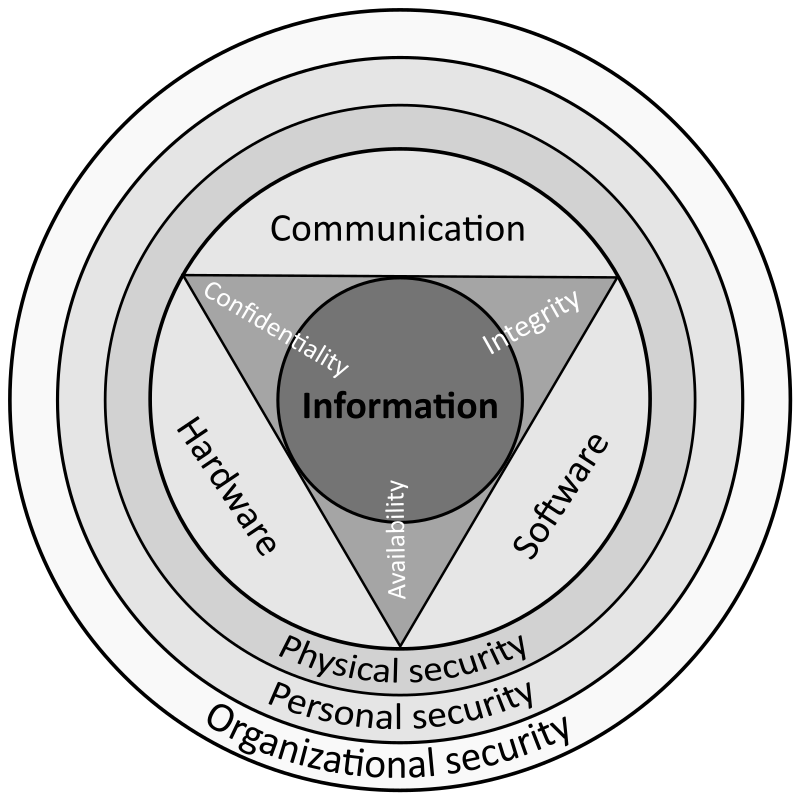
Chapter 5-Protecting Your System: Physical Security, from Safeguarding Your Technology, NCES Publication 98-297 (National Center for Education Statistics)

FTC on Twitter: "Practicing safe physical security should always be a priority – whether at the office, when traveling, and at all points in between. Don't leave computers or phones unattended and