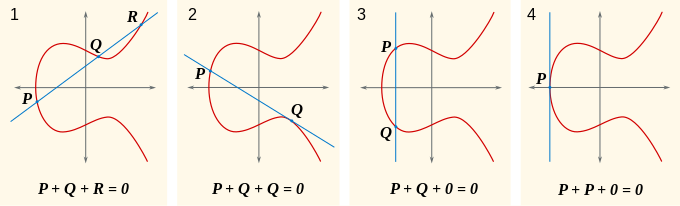
![CSIDH ['si:,sad] Using supersingular elliptic curves to speed up CRS key agreement (joint work with T. Lange, C. Martindale, L. Panny, J. Renes) PQCRYPTO. - ppt download CSIDH ['si:,sad] Using supersingular elliptic curves to speed up CRS key agreement (joint work with T. Lange, C. Martindale, L. Panny, J. Renes) PQCRYPTO. - ppt download](https://slideplayer.com/slide/15511371/93/images/2/Quick+overview+Isogeny-based+cryptography+%3D+new+kind+of+elliptic+curve+cryptography%2C+supposed+to+be+resistant+against+quantum+computers..jpg)
CSIDH ['si:,sad] Using supersingular elliptic curves to speed up CRS key agreement (joint work with T. Lange, C. Martindale, L. Panny, J. Renes) PQCRYPTO. - ppt download
Supersingular Isogeny Diffie-Hellman (SIDH) for Post Quantum Computer Key Generation | by Prof Bill Buchanan OBE | Coinmonks | Medium


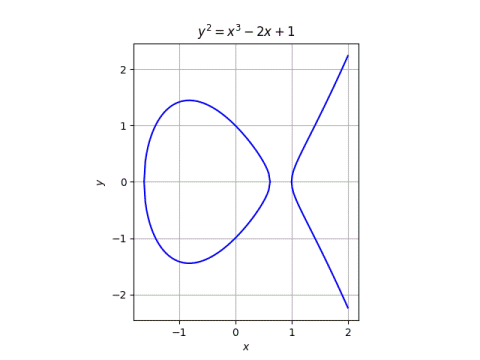





![PDF] INTRODUCTION TO ELLIPTIC CURVE CRYPTOGRAPHY | Semantic Scholar PDF] INTRODUCTION TO ELLIPTIC CURVE CRYPTOGRAPHY | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/545081ddc0484503d95d4cf4c7c4b4bcf17beade/6-Figure1-1.png)