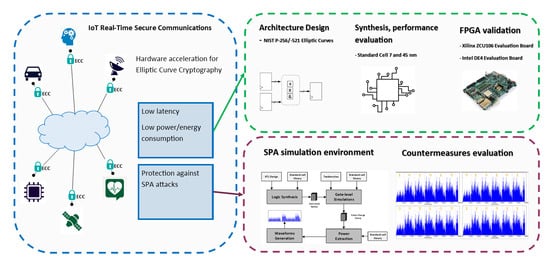
Ensure that the best encryption practices are implemented for your organization with Elliptic Curve Cryptography | Encryption Consulting

Elliptic Labs Launches Virtual Smart Sensor Presence Solution for Low-Power Laptop Security | Business Wire